Welcome
We provide businesses with the tools and support to confidently navigate the law.
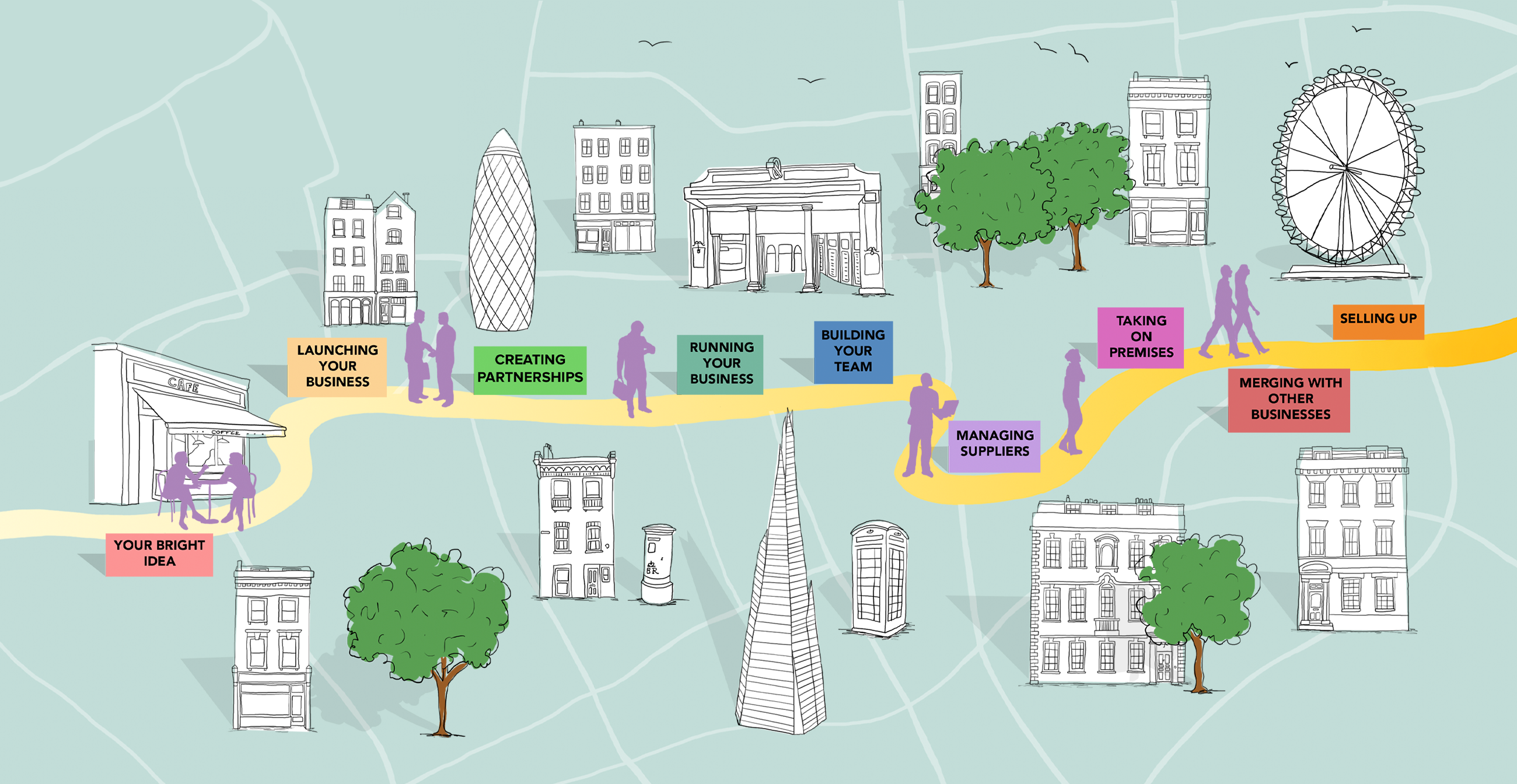
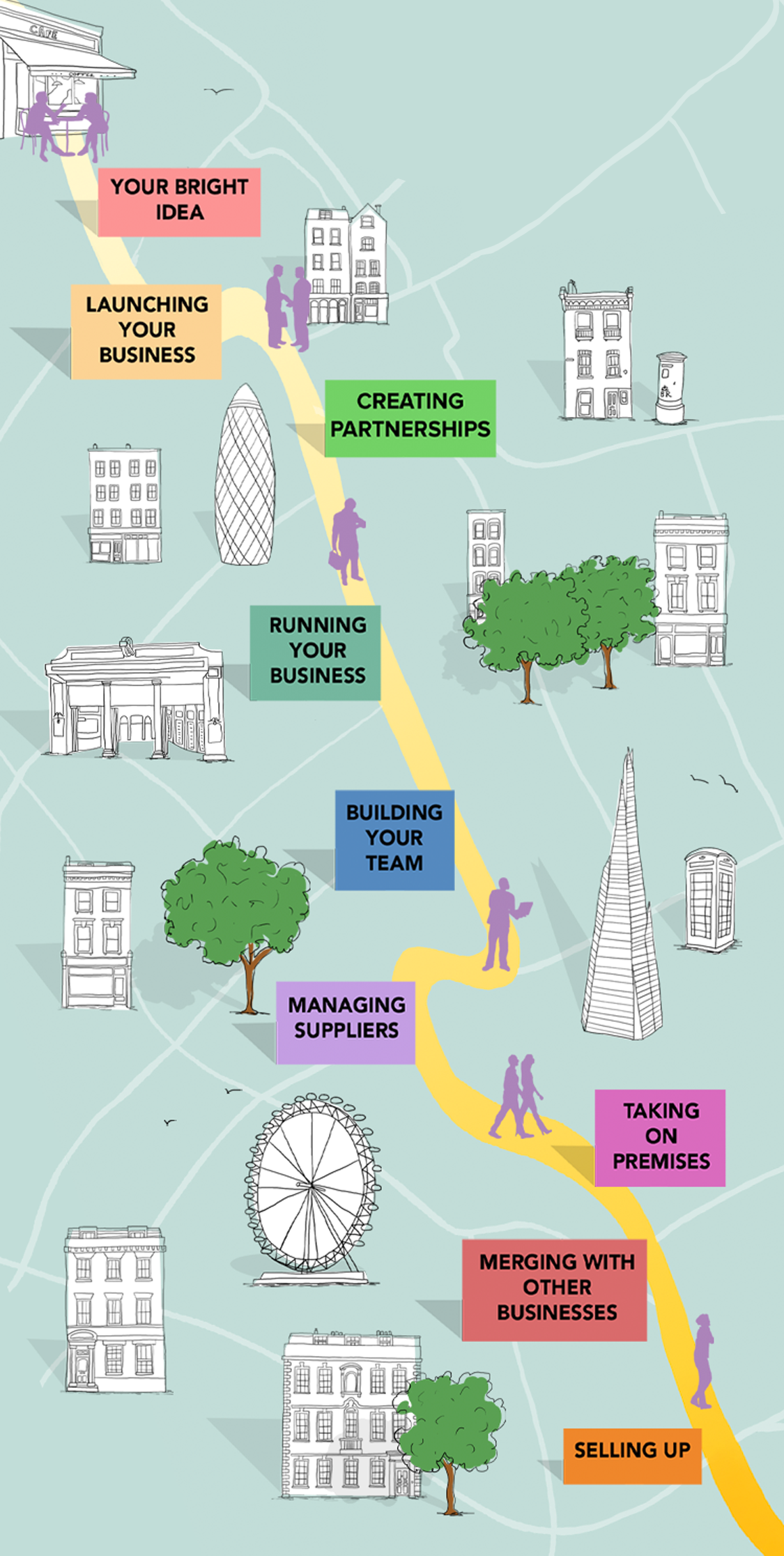
Off To See My Lawyer is a boutique legal practice which has been advising small business for over 20 years. Established by entrepreneur and lawyer Joanna Tall, OTSML provides a cost-effective legal service ensuring businesses are legally compliant and protected. From ready-made legal documents for start-ups to bespoke advice for growing businesses, we are on hand to guide/support clients at every stage in their journey.
We believe legal advice should be friendly, informative and fun. That’s why our clients partner with us for the long term, and that’s why our flexible service is a must-have for any small business.
From the document shop
-
Website Terms of Use
£90.00 +VAT Add to basket -
Privacy and Cookie Policy
£345.00 +VAT Add to basket -
Terms of Sale Online (for goods)
£150.00 +VAT Add to basket -
Entrepreneur’s GDPR Guide
£129.00 +VAT Add to basket
Learnings from an entrepreneur
Meet the inspirational people behind some of the UK’s most interesting, and successful small businesses

Interview with Nicky King, founder of children’s toys, gifts and interiors brand Bobby Rabbit
Latest news
as seen in...